See our complete list of top database security vendors
Bottom Line
Imperva offers a comprehensive solution for database security and compliance. For those requiring data masking, Imperva SecureSphere includes this as an added feature, and built-in analytics add to its allure. However, SecureSphere lacks encryption capabilities, and multiple products must be deployed for comprehensive database security. The core market is medium and large regulated enterprise organizations with compliance requirements.
Product Description
Imperva SecureSphere assesses and helps mitigate organizational database risks and detects compliance and security policy violations that lead to penalties or data breaches. It answers questions such as: where sensitive data lives, who is accessing what data, and whether that data access activity is good or bad. Pre-built behavior analytics and machine learning help detect and prioritize high-risk data access incidents. It also offers data de-identification and anonymization capabilities via static data masking.
KuppingerCole says multiple products must be deployed for comprehensive database security, including SecureSphere Database Security (data discovery, activity monitoring, threat protection, audit and reporting, Camouflage Data Masking (static masking of sensitive data) and CounterBreach (unified security intelligence, behavior analytics and identification of compromised endpoints).
Database Security Features Rated
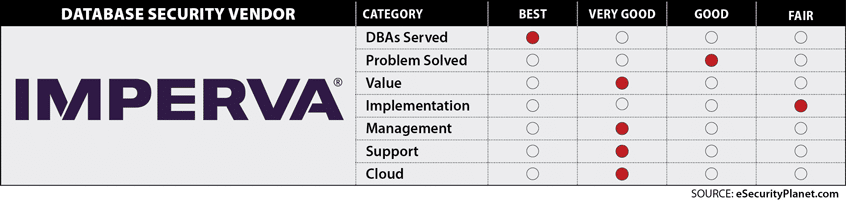
Databases served: Best in class, with support for:
- Oracle (Including NDE/ASO, SSL), Oracle Exadata
- Microsoft SQL Server
- MSSQL
- IBM DB2 (on LUW, z/OS and DB2/400), IBM IMS on z/OS, IBM Informix, IBM Netezza
- SAP Sybase (ASE, IQ, SQL Anywhere)
- SAP-HANA
- Teradata
- MySQL
- PostgreSQL
- Progress OpenEdge
- Maria DB
- Cloudera Enterprise (HDFS, HIVE, HBASE, Impala)
- Hortonworks (HDFS, HIVE, HBASE)
- IBM BigInsights (HDFS, HIVE, HBASE)
- MongoDB
- Cassandra
- Amazon Web Services, Amazon RDS
- Microsoft Azure, Microsoft Azure SQL
- And more
Problem Solved: Good
SecureSphere helps organizations reduce data breach risk and comply with various data privacy and safeguard regulations such as GDPR and PCI. It achieves this through automatic and continuous monitoring and assessment of database risks, the detection and avoidance of inappropriate access and potential data breach events before they happen, and support for industry requirements and proof of compliance auditing.
Value: Very good
Imperva SecureSphere delivers value because of its scalability and flexibility.
SecureSphere provides “low total cost of ownership and high ROI,” said a Director of Security Engineering in the finance industry.
Implementation: Fair
Users deploy an appliance-based management system (physical or virtual) that continuously scans and monitors databases and user database access according to policies that the customer wants followed.?The behavior analytics sit on top of database activity monitoring and filter the granular events captured, highlighting the ones that are most critical.
The length of time for deployment depends on a variety of factors in the environment, but a typical deployment occurs over the course of several weeks. It may be manageable for experienced IT teams but challenging for others.
Management: Very good
Imperva SecureSphere offers centrally managed database audit and protection across traditional on-premises relational databases, big data platforms, and cloud database services. SecureSphere:
- Significantly reduces the amount of security alerts to a more manageable actionable number of highly relevant incident notifications
- Detects threats more accurately by reducing the amount of false positives that overwhelm the security team
- Offers executive dashboard views that enable ease of consumption and visibility
Support: Very good
“Imperva excels at customer service and partnership. Any technical issue we’ve had, we’ve immediately had the full attention of Imperva,” said a CIO in education.
Cloud Features: Very good
Imperva SecureSphere can protect database assets deployed in the cloud, on-premises, or as a service (e.g. Amazon RDS).?The solution can also be deployed in the cloud as virtual appliances in AWS, Azure and other cloud environments.
Intelligence
Imperva SecureSphere utilizes machine learning and behavior analytics to pinpoint and prioritize high-risk incidents, and provides actionable insights that allow security staff to accelerate incident investigation and response. Once unauthorized or inappropriate data access is identified, users can immediately quarantine or block the user access in real-time. SecureSphere also provides automated data discovery and classification with customizable security policies, as well as database vulnerability assessment capabilities.
Delivery
Imperva SecureSphere is available via physical or virtual appliance.
Agents
Data activity can be gathered using a network transparent bridge, a non-inline sniffer, or a lightweight database agent.
Pricing
Pricing is based on a per server approach, and the starting point includes a minimum of 8 database servers. Forrester Research did a study on cost versus ROI for Imperva SecureSphere and found the following benefits of $3.6 million over three years versus costs of $2.3 million, an ROI of 57%, and a payback period of 16 months.








