A report last week by the New York Attorney General’s Office put a spotlight on the ongoing threat of credential stuffing, a common technique used by cybercriminals that continues to spread and is helping to fuel the push for security practices that don’t involve usernames and passwords.
AG Letitia James’ office ran a months-long investigation into credential attacks in the state, uncovering credentials for more than 1.1 million online accounts at 17 companies, including online retailers, restaurant chains and food delivery services, according to the report.
The investigation highlighted the ease with which credential stuffing can be used by bad actors and how often such attacks go undetected. According to James’ office, investigations by the 17 companies – none of which were named – found that most of the attacks hadn’t been detected. All the companies either implemented or planned to put in place additional protections against credential stuffing, the report said.
Password Reuse
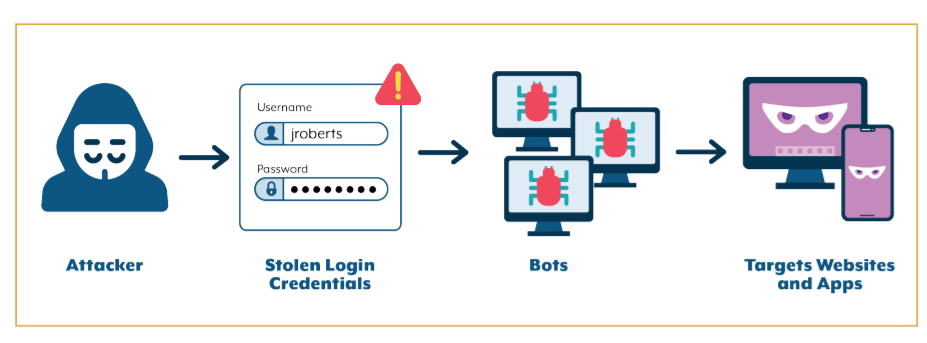
Credential stuffing involves cybercriminals using usernames and passwords stolen from one website to try to log into other websites, at times using a botnet to accelerate the number of attempts. Successful attackers can then use the credentials to leverage stored credit card data to make fraudulent purchases, steal gift cards saved on the customer’s account, use the information in phishing attempts against victims or sell the login information and personal data to other bad actors.
“Virtually every website and app uses passwords as a means of authenticating its users,” investigators wrote in the report. “Users – forced to contend with an ever-expanding number of online accounts they must manage – tend to reuse the same passwords across multiple online services. Unfortunately, the widespread use and reuse of passwords has made them attractive targets to cybercriminals, who know that passwords stolen from one company may provide the keys to a host of accounts at another.”
They noted that unlike “many other types of cyberattacks, credential stuffing attacks often require little technical knowledge to mount. Attackers typically use free, easily accessible software capable of transmitting hundreds of login attempts simultaneously without human intervention. A single attacker can easily send hundreds of thousands, or even millions, of login attempts to a single web service.”
Also read: Best Password Managers & Tools
Removing the Guesswork for Cybercriminals
Leveraging credentials has only become easier in recent years, according to Alicia Townsend, technology evangelist with identity management firm OneLogin.
“Cybercriminals no longer need to randomly guess passwords when they can easily purchase an extensive list of usernames and passwords that have been captured from various systems,” Townsend told eSecurity Planet. “These criminals can then count on the fact that users routinely use the same username-password combinations to get into the dozens – possibly hundreds – of applications they need to provide credentials for and use the same credentials to try and hack into other systems.”
Credential stuffing has become a steadily popular attack tool for bad actors. According to a report by content delivery network specialist Akamai, there were 193 million such attacks worldwide in 2020, with two notable attacks coming in January and May 2021, when credential stuffing attack traffic cruised past 1 billion attacks for each day.
The NY AG’s report cited a 2017 Ponemon Institute report that found that businesses were losing about $6 million a year to credential stuffing attacks due to application downtime, lost customers and increased IT costs.

Monitoring Online Communities
The NY AG’s investigation involved several months of monitoring online communities known for credential stuffing. Investigators said they found thousands of posts containing login credentials that had been used in attacks. Each of the 17 unnamed companies in the report was alerted to the attacks and urged to investigate.
James’ report also outlines steps businesses can take to better detect, protect against and respond to credential stuffing. Those include using bot-detection software and multi-factor authentication, preventing customers from reusing passwords that have previously been compromised, monitoring customer and account activity and leveraging threat intelligence.
There are other steps, such as re-authenticating when a purchase is made and using third-party services to detect fraud, and if there is an incident, conducting timely investigation, remediating the problem, and notifying customers.
See also Best Identity and Access Management (IAM) Solutions
Hackers Use Multiple IP Addresses
Ray Kelly, a Fellow at NTT Application Security, noted that a common tactic for hackers to avoid detection is to use multiple different IP addresses.
“While many sites have request throttling and blocking capabilities, the use of different IP addresses avoids the detection, thereby letting the cyber criminals try as many usernames and passwords as possible,” Kelly told eSecurity Planet.
He pointed to the Have I Been Pwned website, which lets users search a database of known breaches to see if their email or phone password has been leaked, which could lead to credential stuffing attacks. “It’s good practice to check this site to see if you need to change your password due to a third-party breach,” he said.
Uriel Maimon, senior director of emerging technologies at PerimeterX, told eSecurity Planet that the NY AG’s office has done a good job protecting consumers and internet users from the consequences of online identity theft.
“They’ve done so not just by investigating attacks as they’ve done here, but also by holding website owners accountable for addressing the repercussions of attacks and informing their customers, such as with recent litigation,” Maimon said, noting a 2020 case in which Dunkin Donuts, accused of failing to investigate ongoing attacks, agreed to notify customers affected by the attacks, reset their passwords and pay for the unauthorized use of their stored value cards. In addition, the company said it would pay $650,000 in penalties and costs.
Joseph Carson, chief security scientist and advisory CISO at cloud identity security firm ThycoticCentrify, told eSecurity Planet that the AG’s report highlights the worsening state of password hygiene.
“Do not ever reuse old or similar variations of passwords,” Carson said. “If you continue to reuse old passwords, it is like leaving your front door open and inviting cybercriminals into your home. … Many password managers are free; start using them. Use unique long passwords such as passphrases and use a password manager to keep all your passwords unique but easy to use.”
He said that for enterprises, “it is also important to move beyond password managers and start a journey to protecting privileged access.”
Moving Beyond Passwords
Some see the report as more evidence that it’s time to move beyond usernames and passwords.
“Every report along these lines just proves again and again that the use of a username and password to get into a system is no longer secure,” OneLogin’s Townsend said. “Different types of authentication must be required, or required in addition to a username and password.”
A growing number of companies, from Microsoft and IBM to Apple, Duo, Okta and Thales, are pushing to make passwords for authentication a relic of the past. Technologies like face, voice and fingerprint recognition, FIDO-2-compliant keys and software tokens and certificates are options. Microsoft for more than three years has been phasing out passwords for many of its accounts and in September 2021 said it was pushing passwordless authentication to all accounts.
“Nobody likes passwords,” Vasu Jakkal, corporate vice president for security, compliance and identity at Microsoft, wrote in a blog post at the time. “They’re inconvenient. They’re prime targets for attacks. Yet for years they’ve been the most important layer of security for everything in our digital lives – from email to bank accounts, shopping cards to video games.”
Further reading: Passwordless Authentication 101








