Data loss prevention (DLP) refers to a set of security solutions that identify and monitor information content across storage, operations, and networks. DLP solutions help detect and prevent potential data exposure or leaks. They apply policies dynamically, manage business data rights, and automate data processes to effectively protect sensitive information. An effective DLP solution provides the security team a complete visibility of their networks.
To determine if the DLP solution is ideal for your organization, explore how it works, its benefits, best practices, deployment considerations, and reliable providers available on the market. Understanding these factors allows you to make informed decisions when adopting a DLP solution for your cybersecurity strategies.
Table of Contents
How Data Loss Prevention Works in 10 Steps
The effective implementation of data loss prevention encompasses proper setup, continuous monitoring, real-time data review, prevention measures, anomaly detection, data visibility, incident response, contextual analysis, and strengthened prevention and remediation procedures. DLP integrates procedures, technology, and people to effectively detect and prevent sensitive data leaks.
The 10 steps outlined below show how data loss prevention works.
1. Initiate Setup & Configuration
This step requires installing and configuring the DLP tool on the organization’s network infrastructure. This also involves integrating it with existing cybersecurity measures such as firewalls, endpoint protection tools, monitoring solutions, and antivirus software to provide comprehensive data protection and threat mitigation capabilities.
2. Monitor Data Streams
DLP tools continuously monitor data within the organization’s network. This includes scanning data in transit between devices or networks, as well as data at rest stored on servers, endpoints, or in the cloud, to ensure comprehensive coverage for detecting and preventing potential data breaches or illegal access.
3. Review Data in Real Time
DLP solutions perform instant analysis of data packets or files as they’re observed. They scan content for sensitive information such as PII, financial data, or intellectual property, allowing for quick identification and response to any data breaches or unauthorized access, hence enhancing the enterprise’s network security and overall compliance initiatives.
4. Implement Prevention Measures
To prevent data loss, the DLP’s measures require the solution to respond quickly when suspicious activity or illegal access is detected. Blocking data access, limiting user privileges, or terminating suspicious processes are all examples of actions that can be taken to reinforce security standards and reduce the risk of data breaches or unauthorized disclosures.
5. Detect Anomalous Activity
DLP systems use AI and ML to quickly detect abnormal behavior. This pertains to deviations from typical data usage patterns, odd access attempts, and suspicious data transfers, allowing for preemptive action to mitigate potential security concerns and protect sensitive information from unauthorized access or data breaches.
6. Enhance Data Visibility
DLP systems provide complete insights into data consumption and flow across the organization’s network, which helps to improve data visibility. This increased visibility facilitates early detection of potential network security attacks or data breaches and empowers calculated measures to mitigate risks and successfully secure sensitive information.
7. Facilitate Incident Response
In the event of a security incident or breach, the DLP solution monitors and reports on data access and movement. This provides security teams with critical insights into investigating and mitigating the damage. DLP allows rapid and effective response behaviors to contain the incident and avoid further compromise of sensitive information.
8. Analyze Security Events
DLP solutions help the security team interpret high-risk activity or behavior by analyzing the type and context of security events. This technique improves awareness of underlying risks, allowing for more informed decision-making to effectively handle security threats and prioritize mitigation actions, ultimately strengthening the organization’s resilience to possible data breaches.
9. Conduct Remediation Activities
If a security event happens, DLP solutions help to address the problem by identifying the root cause and advising relevant steps. This involves putting corrective measures in place to reduce future risks, thereby encouraging a proactive approach to protecting sensitive data and adhering to regulatory compliance standards inside the organization.
10. Strengthen Threat Prevention Measures
DLP enhances threat prevention by evaluating high-risk behaviors and delivering its insights to security professionals. This enables the refining of security policies, the deployment of new controls, and the improvement of employee training programs in order to effectively reduce potential risks and protect sensitive data from illegal access or exposure.
Why Should Companies Invest in Data Loss Prevention?
DLP promotes risk reduction and endpoint security by classifying and monitoring sensitive data, detecting and blocking suspicious activity, automating data classification and compliance management, and increasing threat visibility. This security approach assists businesses in preventing data breaches, safeguarding sensitive information, ensuring compliance, and protecting against emerging cyberthreats.
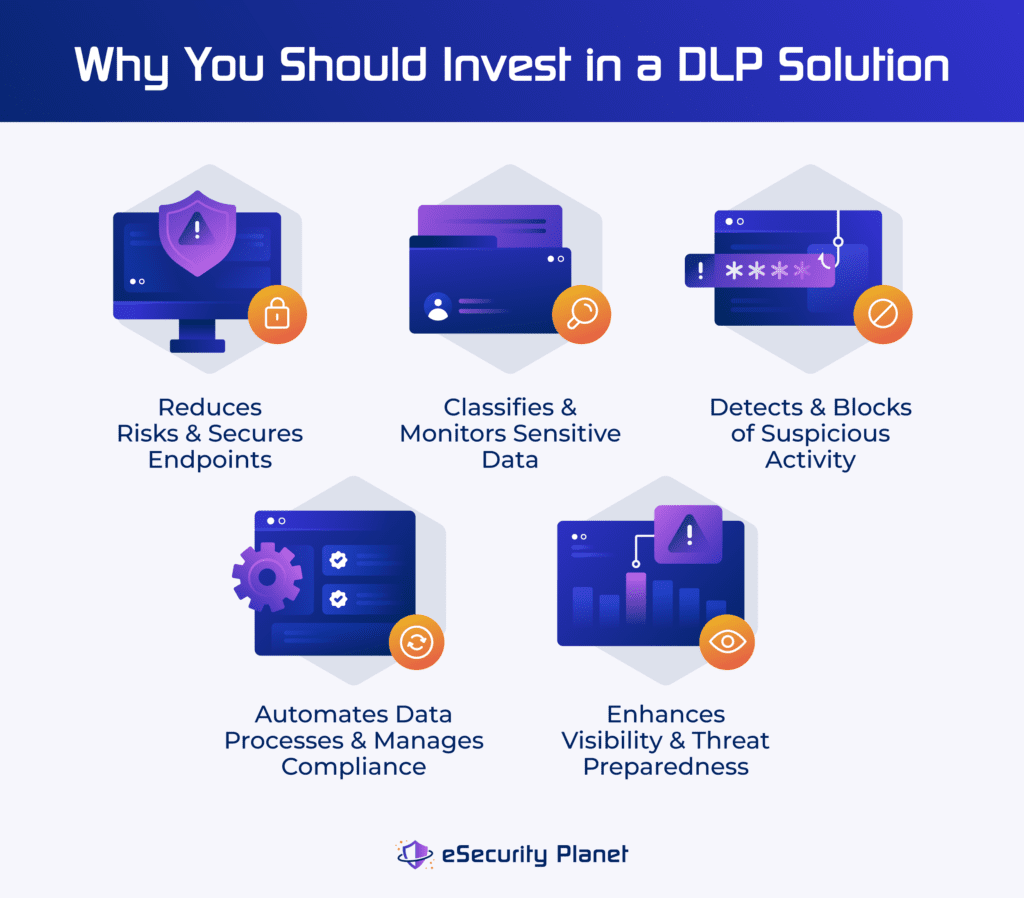
Risk Reduction & Endpoint Security
Implementing DLP solutions lowers the risk of data breaches by protecting endpoints and preventing unauthorized access. This improves overall cybersecurity posture, especially on devices that are sensitive to threats. DLP enforces security regulations, protects data, and monitors usage for compliance and risk mitigation.
Sensitive Data Classification & Monitoring
DLP provides sensitive data classification and monitoring, ensuring regulatory compliance while also protecting intellectual property and consumer information. DLP detects suspicious activity in real time by continuously monitoring data consumption and access, allowing for proactive risk reduction while also boosting network security posture and data governance procedures within businesses.
Detection & Blocking of Suspicious Activity
DLP solutions use advanced detection capabilities to identify and prevent suspicious activity across email, the web, and removable storage devices. DLP uses content inspection, behavior analysis, and machine learning to detect abnormalities that indicate data breaches or policy violations. When detected, automated response steps, such as stopping data transmission or producing notifications, avoid data loss and maintain confidentiality.
Automation & Compliance Management
This DLP capability guarantees accuracy and efficiency in extensive environments. DLP solutions automate data classification based on policies and regulations, utilizing metadata elements to accurately identify sensitive material. This real-time protection, along with powerful reporting and auditing capabilities, makes enterprises easily demonstrate compliance.
Improved Visibility & Threat Preparedness
DLP boosts visibility into data access and usage, supporting continuous threat detection and mitigation. It helps businesses spot emerging security trends, user behavior patterns, and vulnerabilities by giving detailed insights into data flows, user actions, and security incidents. With this knowledge, businesses can efficiently respond to incidents and limit the consequences of data breaches and cyberattacks.
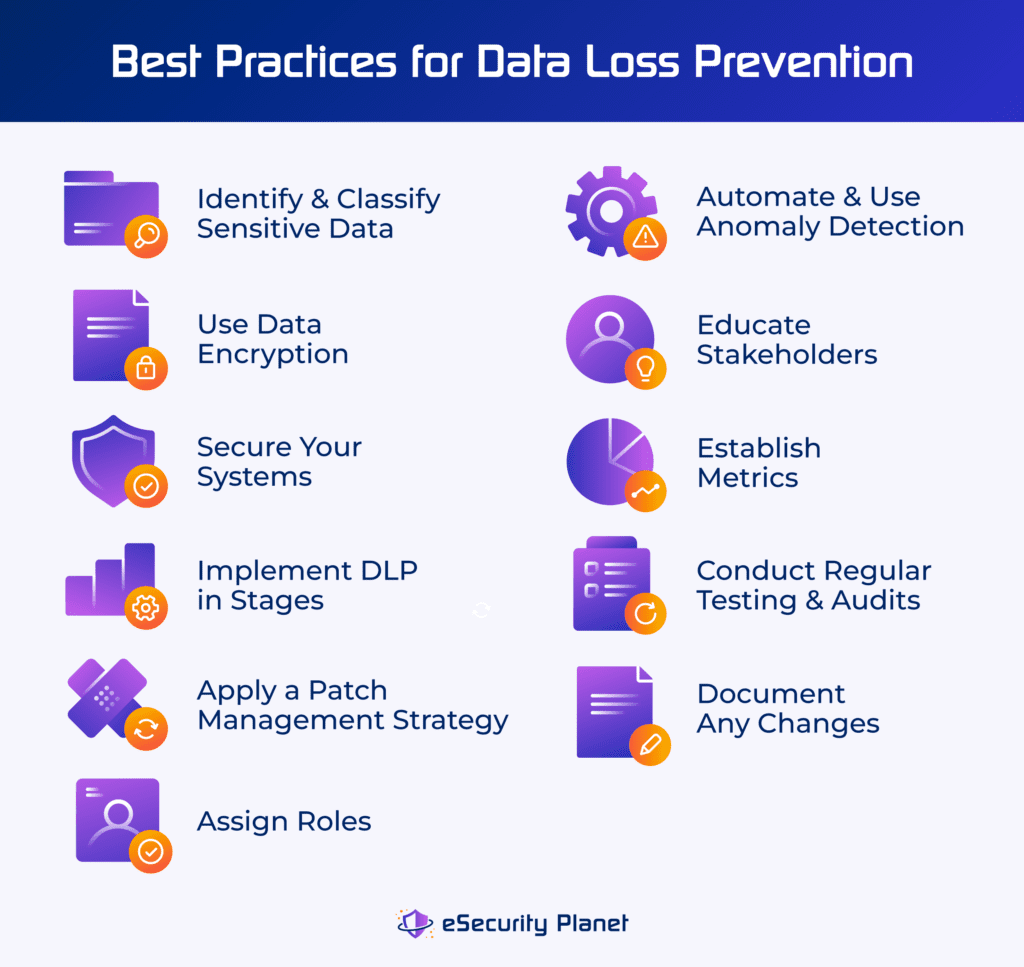
Data Loss Prevention Best Practices
DLP best practices ensure that sensitive data is properly identified, classified, and protected. Additionally, educating stakeholders and conducting regular security testing enhance overall data protection while reducing the likelihood of breaches.
Follow these best practices to establish a successful data loss prevention strategy:
- Identify and classify sensitive data: Label and safeguard sensitive data with DLP policies to prevent unauthorized access or disclosure.
- Use data encryption: Encrypt data at rest and in transit to prevent unauthorized access and preserve the confidentiality and integrity of sensitive information.
- Secure your systems: Increase security by restricting system access to authorized users. This lowers the possibility of unauthorized data breaches or system compromises.
- Implement DLP in stages: Gradually integrate DLP capabilities, aligned with corporate priorities, to successfully fulfill data protection requirements over time.
- Apply a patch management strategy: Apply fixes on a regular basis to resolve vulnerabilities and limit the risk of exploitation by cyberthreats.
- Assign roles: Define roles for data security to enable accountability and effective management of tasks within the organization’s security architecture.
- Automate and use anomaly detection: Use automation and machine learning to quickly identify and respond to potential security breaches.
- Train stakeholders: Educate your stakeholders and users to understand and carry out their data protection duties, and promote a culture of data security awareness.
- Establish metrics: Monitor key indicators to determine the effectiveness of your DLP strategy. This enables data-driven decision-making and ongoing improvement of data security.
- Conduct regular testing, audits, and document changes: Perform audits to validate DLP efficacy. Document configuration on a regular basis and ensure its alignment with your business needs and security standards.
DLP Adoption and Deployment Considerations
When adopting and deploying a data loss prevention solution, businesses must take into account budget, compliance, security needs, scope, trusted partners, team expertise, and more. Regardless of the size or industry of the organization, a thorough assessment guarantees smooth implementation, regulatory compliance, and reliable sensitive data security.
Consider these key factors:
- Budget: Allocate a budget for a DLP solution that balances long-term usability with affordability. Make sure that the appropriate features meet your security requirements within financial limits.
- Compliance: Integrate DLP with governance, risk, and compliance (GRC) solutions for smooth regulatory alignment and effective regulatory compliance processes within the organization.
- Security requirements: Define security methods to protect sensitive data, including intellectual property and personal information. Check if adequate data security procedures are in place.
- Scope: Thoroughly assess data locations and visibility for comprehensive protection measures. Include all sites where sensitive data is stored within the organization’s infrastructure.
- Deployment documentation: Create documentation defining deployment methods and audit records to facilitate successful implementation and knowledge transfer among team members.
- Roles and duties: Define specific responsibilities and roles to establish accountability and prevent data exploitation, ensuring that each team member understands their part in data protection.
- Reporting: Employ reporting tools to obtain insight into data protection and access, which is critical for ensuring compliance with rules and governance standards inside the company.
- Reliable DLP provider: Conduct extensive research to evaluate vendor capabilities, scalability, and compatibility with your current infrastructure. Your vendor solution should provide complete features and support for the implementation process.
- Team expertise and business size: Take into account the product’s complexity and the team’s skills to guarantee an efficient implementation that is tailored to the size and requirements of the business.
3 DLP Providers to Help Safeguard Your Data
Select a suitable data loss prevention solution that meets your organization’s specific needs. Generally, this should include evaluating their data protection capabilities, integration with current systems, and full regulatory compliance support. Make sure that their capabilities are tailored based on the organization’s specific operational environment and goals.
Explore Forcepoint, Symantec, and Proofpoint — three of our recommended DLP providers listed below.

Forcepoint DLP
Forcepoint DLP offers complete features for administering global policies across all main channels, including endpoint, network, cloud, web, and email. It provides established templates, policies, and incident management that improve visibility and control over data and work environments. This allows enterprises to efficiently handle the risks of data loss by safeguarding data wherever it’s accessed or kept.
Forcepoint DLP offers a 30-day free trial. For detailed pricing information, contact Forcepoint’s sales team.
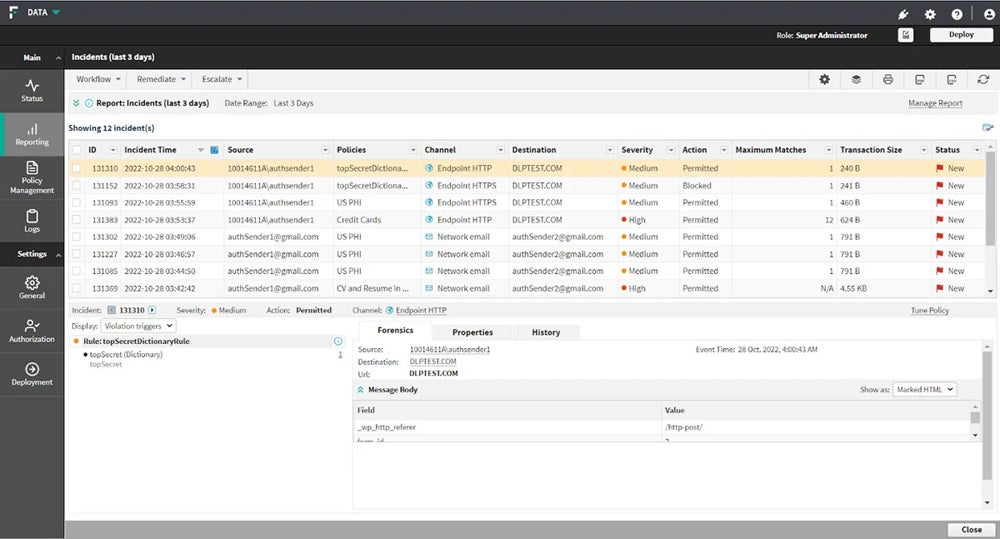

Symantec DLP
Symantec Data Loss Prevention, acquired by Broadcom, is ideal for protecting large networks. It includes Symantec DLP Core and DLP Cloud, which provide cloud connections for web gateways and cloud access security broker (CASB) controls. It offers full protection for businesses, focusing on data security across vast networks, data integrity, and regulatory compliance.
To request for a pricing quote, contact Broadcom’s sales team or their authorized distributors.


Proofpoint Enterprise DLP
Proofpoint’s Enterprise DLP platform excels in standalone email protection, including Endpoint and Email DLP solutions. With a people-centric approach, it combines content, behavioral, and threat awareness to provide granular visibility into data interactions. With capabilities including real-time detection, prevention, and response to data loss situations, it delivers strong protection across endpoints and email channels.
Access Proofpoint Enterprise DLP’s free trial and pricing information by contacting their sales team.
For the comprehensive list of our recommended providers, along with their pricing, offerings, and more, refer to our buyer’s guide on the top data loss prevention solutions.
Bottom Line: Secure Sensitive Assets with Data Loss Prevention
Organizations may classify, monitor, and secure sensitive data across endpoints and networks by putting in place effective DLP solutions. These solutions provide proactive detection and response capabilities. DLP uses powerful analytics and machine learning algorithms to detect unusual activities and policy violations in real time, allowing security teams to take rapid action to prevent data loss or illegal access.
While DLP solutions play a vital role in data protection, they alone can’t guard your whole system’s security. Complement DLP with tools like EDR and SIEM so you can form a holistic security framework that reduces risks and protects your critical information.