Steganography, derived from Greek words meaning “covered” and “writing,” has been used for centuries to hide secret messages inside regular documents.
In cybersecurity, steganography mainly consists of hiding malicious payloads or secret information inside seemingly harmless files such as images, PDFs, audios, videos, and many other document types.
While steganography is often considered something of a joke in capture-the-flag (CTF) events and other cybersecurity defense activities, it can happen in real attacks and can take security defenses by surprise simply by using another layer of cover. For example, hackers attacked Jeff Bezos, CEO of Amazon, with malicious code hidden in a media file and managed to gather confidential information.
What’s the Point of Digital Steganography?
Unlike encrypted communications, which can look immediately suspicious to defenders and detection tools, steganography allows hackers to hide data in a way that would be difficult to easily catch.
In fact, to even be able to catch steganography, you first have to know the technique, and then you have to know which file(s) to analyze. Without this knowledge, users become more vulnerable to malicious script triggers that can be hidden in common file types, such as .gif, .png, .jpg, and others, that don’t typically raise any security alerts.
Also read: Top Endpoint Detection & Response (EDR) Solutions
How Does Image Steganography Work?
Attackers can use the least significant bits of an image to conceal malicious code, leaving the image visually unmodified. This process is often called steghide.
Here is a basic example using Kali Linux and the steghide software. With a simple steghide embed, a text file can be hidden inside the image:
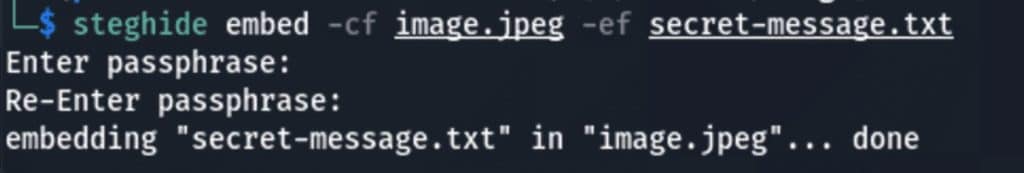
After the process, the naked eye won’t perceive the difference in the modified pixels. The original image is the cover image, and the modified one is called the stego image.
Thanks to an encryption algorithm, the message or the malware is embedded in the image by altering only specific pixels.
Steganalysis is the act of decoding the stego image. With a simple steghide extract, the secret .txt file can be placed in another folder:
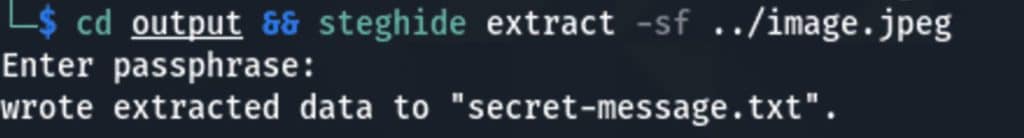
Note that a passphrase isn’t used in the example. It’s not mandatory, but you would likely add one in real circumstances. Otherwise, anyone could extract the secret message.
The command lines are pretty straightforward, and you can even use software such as Stegosuite to do the same operations with a graphical interface.
How Hackers Use Steganography
Don’t underestimate the power of steganography. Even if it’s only to hide a text message, it’s a powerful technique to evade detection or communicate privately while using public networks.
An image is a pretty good asset to hide malicious code and information. It does not raise curiosity, and most security tools do not flag such file types.
However, a typical attack can use other file types, such as macro-enabled Excel and Word documents with embedded PowerShell or bash scripts.
The victim opens the file to read it but triggers a hidden script that installs a downloader somewhere on the computer. This downloader connects to the internet to get anything the hacker wants to compromise on the machine (e.g., malware or command-and-control instructions).
LokiBot is a striking example. This Trojan horse had multiple variants, but several used steganographic images to hide malware. In one variant, the hackers bypassed most email security gateways by hiding malicious .zipx attachments inside images.
In 2020, a campaign relying on steganographic documents affected companies in the U.K., Germany, Italy, and Japan.
The hackers managed to bypass security checks by infecting an Excel document with a steganographic image hosted on legitimate platforms such as Imgur. The image contained a hidden script that downloaded Mimikatz, a program that steals Windows credentials.
Also read: How to Prevent Ransomware Attacks: 20 Best Practices for 2022
How to Protect Against Steganographic Documents
Steganography can be a nightmare for anti-malware tools. Theoretically, you cannot know whether an image is steganographic or not until you inspect it manually.
Still, if the image is abnormally heavy or has a significant amount of duplicate colors, it’s a huge warning sign. Other signs forensic teams can use to identify common hiding techniques include:
- Malicious code at the end of a file
- Unusual file signatures or properties
- Known algorithm such as LSB (least significant bit)
Alternatively, there are various techniques to spot unusual alterations automatically, such as statistical or structural analysis, but CDR (content disarm and reconstruction) solutions seem way more efficient.
This technology removes malware automatically. Instead of detecting steganographic documents, you define stricter policies for various endpoints, file formats (including images), and sources such as emails.
Any non-approved object in files, such as macros or malicious scripts, gets removed quickly without impacting employee productivity.
Steganography Techniques Evolve Quickly
More sophisticated approaches may now involve artificial intelligence to create steganographic images using adversarial training. In that perspective, the steganogan package (Python) can be helpful to understand how it works.
It uses a trained model to hide information instead of classic steganographic techniques. This way, there won’t be recognizable artifacts for steganalysis.
Behind the scenes, the tool uses multiple functions to optimize encoding and decoding. In this case, defenders would have to train a model too. Otherwise, the detection rate will be low, as the encoding method is unknown.
It can be done, for example, by generating lots of steganographic images with various parameters and instances to create rich datasets to better detect sophisticated steganographic documents.
The best defense against this threat, then, might be behavioral security tools that detect any unusual activity on your network. Those tools are available as standalone UEBA products, and increasingly behavioral detection capabilities are showing up in other cybersecurity tools like EDR.
Read next: Best User and Entity Behavior Analytics (UEBA) Tools








