A previously unknown but highly skilled Chinese-speaking cyberespionage group is using sophisticated malware to attack government and private entities in Southeast Asia through a long-running campaign that targets systems running the latest versions of Microsoft’s Windows 10.
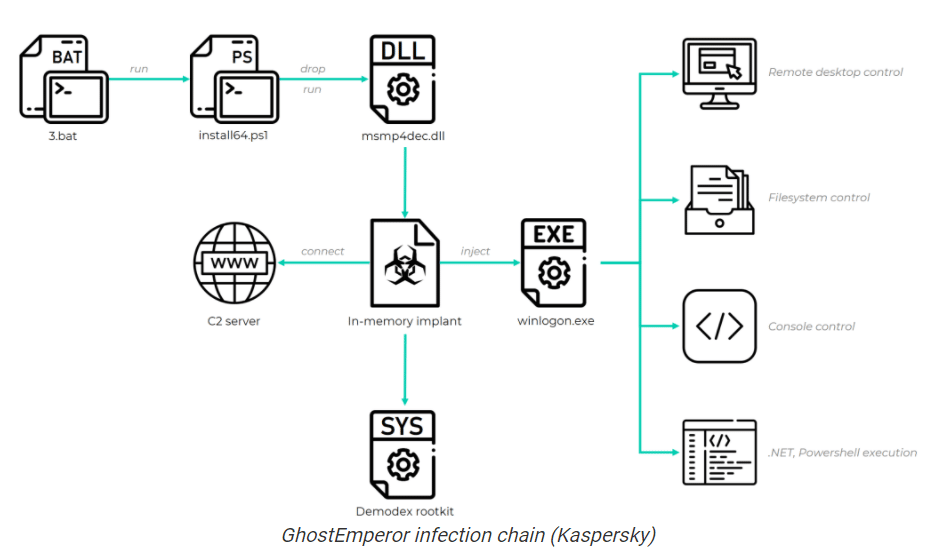
The group – which researchers with Kaspersky Lab are calling GhostEmporer – uses a multi-stage malware framework designed to give the attackers remote control over the targeted servers. At the same time, GhostEmperor leverages the rootkit – which they named Demodex – as a backdoor into the servers to help the malware evade detection and ensure a long-running operation on the infected machines.
The Kaspersky researchers first wrote about GhostEmperor in July and rolled out another blog this week.
“With a long-standing operation, high-profile victims, advanced toolset and no affinity to a known threat actor, we decided to dub the underlying cluster GhostEmperor,” they wrote in the latest blog. “Our investigation into this activity leads us to believe that the underlying actor is highly skilled and accomplished in their craft, both of which are evident through the use of a broad set of unusual and sophisticated anti-forensic and anti-analysis techniques.”
Rootkit Uses Cheat Engine Scanner
The Demodex rootkit is used to hide the malware’s artifacts from investigators and security products. It includes an undocumented loading scheme involving the kernel mode component of an open source project named Cheat Engine to bypass the driver signature enforcement mechanism in Windows, they wrote. Cheat Engine is a memory scanner and debugger developed for Windows that has been used to help users evade detection.
“This tool is fairly advanced because it bypasses security features intended to prevent the loading of unsigned device drivers,” Jake Williams, co-founder and CTO of incident response solution vendor BreachQuest, told eSecurity Planet. “It does so by using a legitimate tool designed to help players of online games cheat [Cheat Engine]. While this tool is itself digitally signed and not malicious, it has no place in the vast majority of environments.”
Organizations should audit their configured services and monitor event logs for the creation and modification of services to detect the creation of the service loading the legitimate – but unexpected – Cheat Engine driver, which is pivotal to the infection chain, Williams said.
Attacks Began in Mid-2020
While recently investigating attacks against Microsoft Exchange servers, Kaspersky researchers saw what they called a recurring cluster of activity on several compromised networks that stood out because of the use of the previously unknown rootkit. They were able to determine that the toolset had been used as early as July 2020 and that the attacks were focused primarily in Southeast Asia – including Indonesia, Malaysia, Thailand and Vietnam – though there were other victims in Egypt, Afghanistan and Ethiopia, including several governmental bodies and telecommunications companies.
While most of the victims were in Southeast Asia, some of the organizations in the other regions had strong ties to countries in Asia, which the researchers took to mean that the attackers may have used those other infections in countries in which they have a geopolitical interest.
GhostEmperor used multiple attack avenues into the systems that resulted in the execution of the malware in memory. The group exploited known vulnerabilities in public-facing server software, such as Apache, Windows IIS, Microsoft Exchange and Oracle. One of the infections of an Exchange server occurred March 4, two days after Microsoft released the patch for the high-profile ProxyLogon vulnerability.
“It is possible that the attackers exploited this vulnerability in order to allow them to achieve remote code execution on vulnerable Exchange servers,” the researchers wrote.
Chinese Threat Actor Suspected
They determined the campaign is being run by an unknown Chinese-speaking threat actor because of the use of open-source tools like Ladon and Mimikat_ssp, which they said are popular with cybercriminals from the region. There also were other indicators, including version information found within the resource section of second-stage loader binaries that included a legal trademark field with a Chinese character.
The use of such sophisticated malware techniques indicates that the cybercriminals have expended a great deal of effort to pull together the malicious toolkit to avoid detection, Archie Agarwal, founder and CEO of threat modeling provider ThreatModeler, told eSecurity Planet.
“Recent research shows criminals remain undetected on networks for an average of 11 days,” Agarwal said. “It should be noted this is an average taken across both advanced and simplistic attacks. This particular group is without doubt highly sophisticated and probably state-supported and so it is no surprise they would remain undetected for long periods.”
For such bad actors, the primary motivation usually is industrial espionage and political advantage, he said, adding that “the sheer sophistication of their operation and malware framework would only be used for high gain and usually supported at the state level.”
GhostEmperor Plays the Long Game
GhostEmperor’s aim was to target prominent organizations and maintain a long-standing and persistent operation, the Kaspersky researchers wrote. They noted that the bad actor was able to keep undetected for months, “all the while demonstrating a finesse when it came to developing the malicious toolkit, a profound understanding of an investigator’s mindset and the ability to counter forensic analysis in various ways.”
The researchers said that businesses and government agencies should sleep on rootkits, whose value as a method of attack has fallen in recent years. The development of Demodex and other recent rootkits show that they can still be used effectively to help attackers avoid detection.
“As we have seen, the attackers conducted the required level of research to make the Demodex rootkit fully functional on Windows 10, allowing it to load through documented features of a third-party signed and benign driver,” they wrote. “This suggests that rootkits still need to be taken into account as a TTP [tactics, techniques and procedures] during investigations and that advanced threat actors, such as the one behind GhostEmperor, are willing to continue making use of them in future campaigns.”
Inventory and Patch
Given that the common entry points were public-facing servers with known vulnerabilities, organizations should make sure to undergo inventories of all public-facing assets as often as possible and ensure they’re patched, ThreatModeler’s Agarwal said.
“Threat actors will conduct intensive reconnaissance looking for these assets and organizations must do likewise,” he said.
Further reading:
Best Patch Management Software & Tools








