Video conferencing vendor Zoom has seen its fortunes soar amid the remote work boom of the last two years, and other cloud collaboration platforms like Microsoft Teams and Cisco Webex have seen demand skyrocket too.
The sharp increase in demand put a focus on security shortcomings in Zoom’s architecture – “Zoombombing” became a thing – that the company was quick to address.
But recent reports by security researchers highlight not only other vulnerabilities in Zoom’s offerings, but also the threat that the connected nature of cloud-based collaboration technologies pose. And with a hybrid workforce that’s likely here to stay, these issues raise bigger questions about security practices in a widely distributed workforce.
A Focus on Zoom
Earlier this month, Natalie Silvanovich, a researcher with Google’s Project Zero bug-hunting initiative, published an analysis of two zero-click vulnerabilities in the video conferencing platform that could have enabled threat actors to take control of a victim’s Zoom clients and multimedia routers (MMRs).
A little more than a week later, cybersecurity firm Armorblox outlined an account takeover attack that leveraged malicious phishing and social engineering.
In Armorblox’s case, Zoom itself wasn’t compromised. Instead, its wide-ranging use by enterprises convinced threat actors to use emails with spoofed addresses to entice victims to unknowingly download a malicious payload.
“With Zoom becoming one of the most prevalent tools for businesses to connect via video conferencing, attackers seized the opportunity to target users with a malicious phishing scam … with the goal of stealing victims’ Microsoft Teams account credentials,” Lauryn Cash, product marketing manager at Armorblox, wrote in a blog post.
Also read:
- Remote Work Security: Priorities & Projects
- Secure Access for Remote Workers: RDP, VPN & VDI
- Best Zero Trust Security Solutions
Vulnerabilities Found on Platform
In her analysis, Project Zero’s Silvanovich noted that with many other video conferencing platforms, one user will initiate a call that others immediately accept or reject. But Zoom calls are usually scheduled in advance and users join through an email invitation.
“In the past, I hadn’t prioritized reviewing Zoom because I believed that any attack against a Zoom client would require multiple clicks from a user,” she wrote. “However, a zero-click attack against the Windows Zoom client was recently revealed at Pwn2Own, showing that it does indeed have a fully remote attack surface.”
Her own investigation found two vulnerabilities, including a buffer overflow that impacted both clients and MMR servers. Another was an information leak that can be used by attackers on MMR servers. Hackers attacking the flaw could target Zoom accounts through connections with Zoom Contacts.
Both vulnerabilities were reported to Zoom, which fixed them on Nov. 24.
Flaws on MMR Servers a Concern
Silvanovich wrote that the vulnerabilities in Zoom’s MMR servers were particularly concerning. The servers process meeting audio and video content, which means that an attacker who compromised the system could monitor any Zoom meetings that didn’t have end-to-end encryption. The servers also lacked address space layout randomization (ASLR), which would make it easier for a threat actor to exploit memory corruption vulnerabilities.
Zoom recently enabled it, she wrote. Still, it was a concern that ASLR hadn’t already been enabled.
“ASLR is arguably the most important mitigation in preventing exploitation of memory corruption, and most other mitigations rely on it on some level to be effective,” Silvanovich wrote. “There is no good reason for it to be disabled in the vast majority of software. … All software written for platforms that support ASLR should have it (and other basic memory mitigations) enabled.”
Zoom’s Broad Use Leveraged in Phishing Attempt
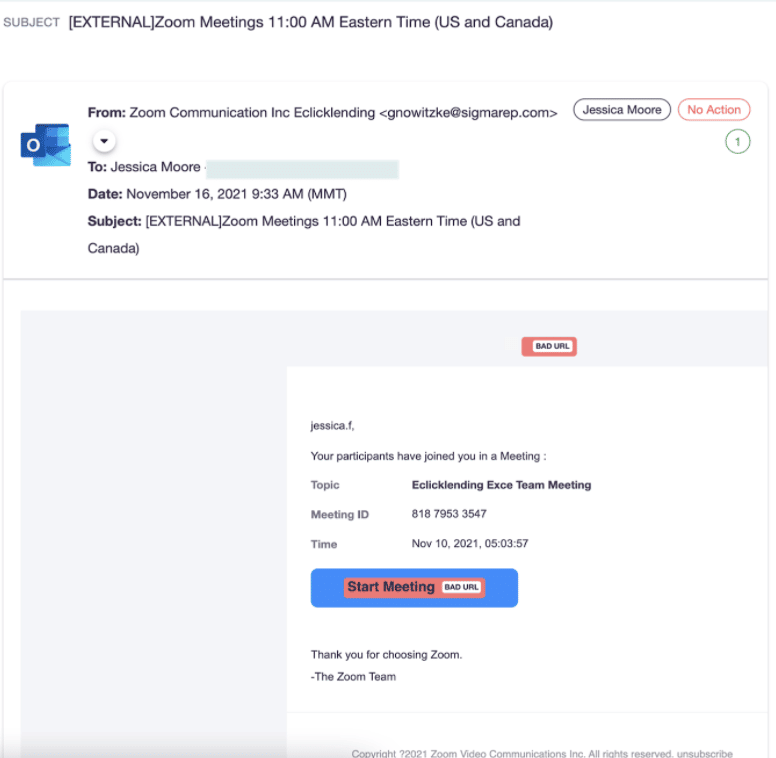
In Armoblox’s research, hackers used email with a socially engineered payload. The attackers tried to spoof the email address and replicate the subject line of a legitimate email from Zoom.
“The email took advantage of the end users’ natural instinct (in any Zoom call) to start the meeting,” Armorblox’s Cash wrote. “When the user clicked on the link to start the meeting, they fell into the trap of the malicious attack and were navigated to a landing page that mimics a Microsoft Outlook login screen.”
The email was able to bypass Microsoft email security controls, she wrote. The emails were able to skip spam filtering because Microsoft’s controls determined they were from a safe sender, to a safe recipient or were from an email source server on the IP Allow List.
About 10,000 emails were sent to an online mortgage brokerage company in North America, according to Armorblox.
Ubiquitous Adoption at Issue
“The ubiquitous adoption of Zoom as the preferred tool for remote collaboration was used by the malicious actor to socially engineer and email as a trusted sender,” Cash wrote. “The specific call to action (CTA), ‘Start Meeting,’ was strategically used due to it being a common business workflow carried out every day.”
That ubiquitous nature and the broad reach within enterprise should not be overlooked as part of the attack surface, according to cybersecurity professionals.
“Zoom accounts and users don’t exist in isolation,” Erkang Zheng, founder and CEO of asset management platform vendor JupiterOne, told eSecurity Planet. “Instead, they’re cyber assets and should be viewed in the context of direct and indirect relationships. A single Zoom account might only be used by one employee; however, that employee is connected to countless other cyber assets, such as Microsoft Teams, devices, cloud resources and sensitive data repositories.”
Zoom, Customers Must Address Risks
Oliver Tavakoli, CTO at cybersecurity vendor Vectra, said many collaboration platforms in many ways are relatively new, making them less familiar to security professionals at companies.
“Tools which organizations use to conduct normal business have always been targets for attackers as any odious activity within such communication channels tends to intermingle with normal traffic patterns,” Tavakoli told eSecurity Planet. “Collaboration platforms, such as Zoom, which during the pandemic have become more central to how businesses operate, are poorly understood by security teams in terms of the attack surface they present. These tools are also relatively immature in terms of accompanying security protections provided by third parties.”
He said it’s incumbent on vendors like Zoom to put more effort into providing greater security controls to lock down their environments and to add more telemetry to monitor it and block attacks.
Social Engineering Not Going Away
Hank Schless, senior manager of security solutions at cybersecurity vendor Lookout, also warned that social engineering will remain a significant challenge for IT and security teams because it not only works for the bad actors but they’re also getting better at it.
“Threat actors know that social engineering is most effective on personal channels such as social media, third-party messaging apps, and even dating apps,” Schless told eSecurity Planet. “Organizations that allow employees to use their own smartphones and tablets for work in a bring-your-own-device [BYOD] scenario are at even greater risk, as employees have both personal and work apps on those devices.”
Applications like Zoom also will continue to be a problem as hackers are increasingly using fake links to commonly used platforms as foundational to phishing campaigns.
“In the age of hybrid work, we’ve been conditioned to automatically click into any link from Zoom, Google Docs, Microsoft Office and more,” he said. “Attackers know this and use the inherent trust we have in seeing those names against us.”
Read next: The Best Wi-Fi 6 Routers Secure and Fast Enough for Business








