Microsoft’s Visual Studio Code integrated development environment (IDE) is used by as much as 75% of developers, so any security issue has widespread implications. And Aqua Nautilus researchers have discovered a big one.
The researchers reported earlier this month that the VSCode editor could be vulnerable to attacks targeting its extensions. The free open source and cross-platform IDE is very easy to use, and there are literally thousands of free extensions developers can install in one click to speed up their work.
These extensions are usually written with Node, and the packages are downloaded from NPM. which makes common supply chain attacks possible against the code editor. Besides, these NPM packages have their own dependencies, so the breach could come from pretty much anywhere in the chain.
The researchers used masquerading techniques to prove their concept. They impersonated Prettier, an extremely popular extension used by developers to format code: “In just under 48 hours, we got more than a thousand installs by active developers from all around the world!”
Even if not all users fell into the trap, thousands of installs is more than enough to do serious damage, like stealing credentials or exfiltrating confidential information.
Researchers Used Classic Typosquatting
Instead of “prettier-vscode,” researchers used “pretier-vscode,” with only one “t,” in the extension URL on the marketplace. It’s easy to make the typo, and only the URL and a few other details differ, as the researchers were able to use the same logo, the same name, the same description, even an exact copy of the original readme.
If a user typed “pretier” in the search bar, they wouldn’t even get the legitimate extension in the list, as only the typosquatted version has this name.
This approach is heavily used by threat actors on other marketplaces such as NPM and PyPI, but malicious VSCode extensions seem to be on the rise, thanks to its dominant market position.
According to researchers, the danger is high for two main reasons:
- anyone can publish an extension which could be listed in the Marketplace
- all extensions run with the privileges of the user that has opened the VSCode without any sandbox
See the Top Code Debugging and Code Security Tools
Identifying Malicious Extensions
It’s not easy to spot malicious extensions. Look at the screenshot below:
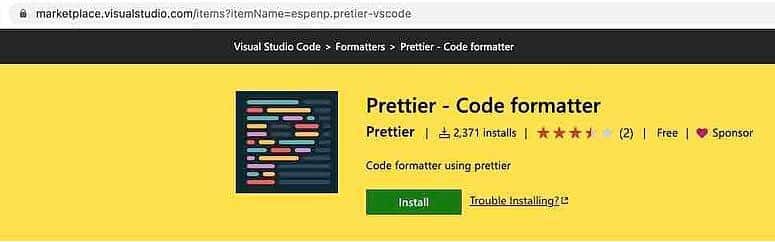
You’ll notice the number of downloads is unusually low for such a prominent extension: 2k vs 27M for the real one. It’s the same for the number of ratings: 2 vs. 370.
However, researchers were able to replicate almost everything else, as display names and titles do not have to be unique on the platform. In addition, the number of downloads or stars could be artificially increased to gain even more credibility.
There are other differences, such as the date of the first release (2022 vs. 2017), but if you miss those details it’s easy to fall into the trap, especially when you lack time to fully vet the source.
Even worse, anyone can get the checkmark “Verified” near to their name just by proving ownership with the domain name of their choice. The term “Verified” could be misleading for many users according to researchers.
All Registries At Risk
The POC looks pretty convincing, but this problem is not specific to the VSCode marketplace. The whole idea with these ecosystems is that anyone can share an extension that can become very popular.
Even if platforms run deep scans to spot viruses and other known malware, nothing prevents an extension from requesting whitelisted (or “not blacklisted”) URLs, such as a seemingly legitimate GitHub repository that contains malicious payloads. These fake repositories get reported and destroyed eventually, but the damage is done.
Researchers also noted that legitimate developers might introduce vulnerable code unwittingly. It’s sometimes hard to distinguish poor code choices from malicious intent.
How to Mitigate the VSCode Threat
It should be noted that this new attack vector has not been observed in the wild yet, which might explain why there’s so little information about it.
The most obvious recommendation for developers is to be extra vigilant when installing any extension to their favorite IDE. Only use trusted sources, but be aware of the common techniques used by threat actors, such as typosquatting and masquerading.
The lack of time excuse is not acceptable in the end. As a developer, you have a responsibility, so it’s worth spending extra time to review your tools carefully.
However, because attackers can leverage other techniques like social engineering to trick their victims into downloading malicious applications, additional measures can help developers to mitigate these threats:
- It’s okay to test a new tool in your free time (in a virtual machine, for example), but not on your work environment.
- Review all requested permissions and capabilities: Why does the program need root access? Is it justified? Are there better alternatives?
- If the extensions need to “run as you,” enumerate your own privileges, and do not hesitate to remove unnecessary permissions if it’s possible. Do you need an administrator account all the time?
- Prioritize sandboxes and other isolation mechanisms: Activate it (it’s not necessarily enabled by default) or install a dedicated package that will confine apps and processes.
- Protect your accounts with MFA/2FA.
Clearly the least privilege principle and containers can help mitigate the threat significantly. For this specific case, users may also leverage “Worskspace trust” and the “Restricted Mode.”

In this mode, extensions might be disabled automatically or have limited functionality.
It’s not magic, though, as it depends on the author’s indications, so it’s unlikely threat actors will “evaluate their extensions for possible security vulnerabilities and declare that they have limited support when running in Restricted Mode,” as VSCode requests.
As a better approach, I would recommend the following to dev teams: Share and discuss new tools or maintain a list of common extensions to install for new members. The good news is that can be scripted and versioned in .vscode/extensions.json:
{
"recommendations": [ "esbenp.prettier-vscode" ]
}
This way, anyone who clones the project repository can install the right extensions automatically.
Read next: How to Prevent Software Supply Chain Attacks








