Hackers got into an email server at the FBI over the weekend to spread fake messages in an attempt to blame a cybersecurity expert for non-existent attacks, apparently in hopes of damaging his reputation.
According to intelligence organization Spamhaus and subsequent reports, the hackers sent out emails with the false accusations in two waves to more than 100,000 addresses, using email addresses gleaned from a number of sources, including a database used by the American Registry for Internet Numbers.
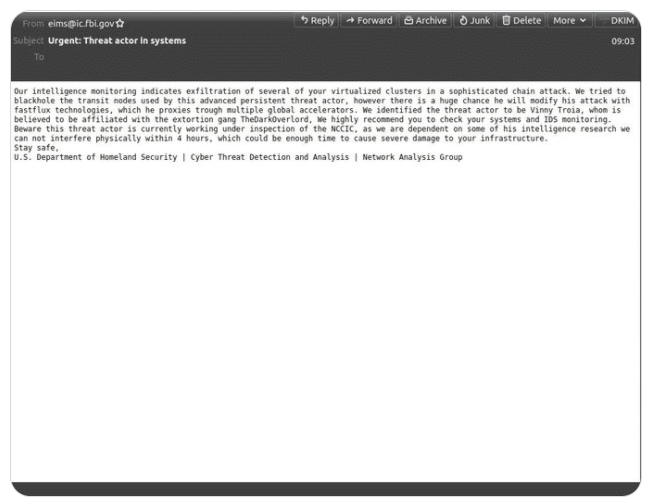
The spam emails included a message that was made to look like it came from the Department of Homeland Security (DHS) and warned the recipient about a “sophisticated chain attack” that had led to the “exfiltration of several of your virtualized clusters.” The emails identified the bad actor as Vinny Troia, whom it said was affiliated with the cybercriminal gang TheDarkOverlord.
Security Expert May Have Been the Target
However, Troia actually is the founder and head of research at cybersecurity firm Shadowbyte and CEO and principal researcher at Night Lion Security. According to a tweet from Marcus Hutchins, a cybersecurity analyst with Kryptos Logic and the author of the MalwareTech blog, Troia also has written a book detailing information about TheDarkLord gang and that, soon after, he became the target of bad actors who hacked his Twitter account and website and had erased ElasticSearch clusters while leaving behind his name.
The hacking of the FBI email server appears to be the latest escalation in the campaign against Troia.
After Spamhaus detected the spam emails and alerted the FBI, the agency said in a statement that both it and the Cybersecurity and Infrastructure Security Agency (CISA) were aware of the hack and had taken down the compromised hardware.
Later the FBI released another statement saying that a software misconfiguration temporarily allowed a hacker to use the agency’s Law Enforcement Enterprise Portal (LEEP) – which is used by the agency to communicate with state and local law enforcement offices – to send the fake emails. FBI officials said that the compromised server was used for pushing notifications for LEEP, wasn’t part of the agency’s corporate email server, and that the bad actor had not been able to access or compromise data on the FBI network.
Also read: How DMARC Can Protect Against Ransomware
FBI Address Used
The emails came from eims@ic.fbi.gov, a legitimate address, according to a tweet from Spamhaus, and from the FBI IP address, 153.31.119.142 (mx-east-ic.fbi.gov).
The software vulnerability was fixed and law enforcement agencies were told to disregard the fake emails. However, because the emails were coming from a legitimate FBI server, they were able to get past many spam filters, causing some concern among recipients and reportedly inundating the FBI with calls.
“As with any communication from the federal government, any recipient of a message should double check with the agency that has allegedly sent the message as to whether the communication is legitimate,” Hank Schless, senior manager of security solutions at cybersecurity firm Lookout, told eSecurity Planet. “Any message that seems to create a high pressure situation is likely some sort of spam or phishing. Attackers want targets to feel like they have nowhere to turn in order to solve the apparent issue at hand.”
Lessons from the Breach
The lessons learned from the attack can be applied broadly, Schless said. Even if the domain from which the email is sent is legitimate or internal, “[if] you feel like it’s something out of the ordinary or high pressure, call the person or organization directly. If the message has a link or attachment embedded, don’t interact with it until you have validation.”
In a tweet, Troia indicated that the bad actor who hacked into the FBI server and sent out the email uses the name “Pompompurin.” Chris Morgan, senior cyberthreat intelligence analyst at cybersecurity firm DigitalShadows, told eSecurity Planet that Pompompurin is a known associate of the ShinyHunters hacker group.
Cybersecurity journalist Brian Krebs noted in his blog that at around the same time the emails began rolling out from the FBI server, his KrebsOnSecurity blog received an email from the same email address saying, “Hi its pompompurin. Check headers of this email it’s actually coming from FBI server. I am contacting you today because we located a botnet being hosted on your forehead, please take immediate action thanks.”
In an interview with Krebs, the bad actor said he wanted to publicize a vulnerability in the FBI’s IT system. One weakness was that until the attack occurred, the LEEP portal let anyone apply for an account, Krebs wrote.
Also read: Email Security for Your Business
Zero Trust Means Having Zero Assumptions
DigitalShadow’s Morgan said there were likely a number of motivations from the attack, including highlighting a security vulnerability, pranking Vinny Troia, and trolling the FBI’s security.
“Many companies would have been rushed into incident response during the early periods of Monday morning, so it appears the actor responsible for the emails will have achieved their goal of creating mischief,” Morgan said. “Any organization receiving the fake FBI notification can ignore its claims and wait for further details to be released by the FBI.”
Lookout’s Schless said the motivation wasn’t clear, but added that “there’s the distinct possibility that the attack could’ve gone straight to social engineering and attempted to get legitimate FBI employees to mistakenly share their login credentials or, in the case of an angle like this, install some sort of fake security app that actually had malware built in. Any organization could fall victim to this type of attack, which is why it’s so critical to understand how your users are interacting with both cloud-based and on-premises apps and infrastructure.”
Joseph Carson, chief security scientist and advisory CISO at ThycoticCentrify, told eSecurity Planet that the FBI hack “is a reminder that cybercriminals will look for techniques to deliver malicious content under the disguise of legitimate services, this time coming from a legitimate FBI email address.”
Carson said that in the emerging world of zero-trust security environments – where nothing is trusted until it’s verified – people need to be sure to verify something like an email, even if it is coming from a legitimate source.
“Remember, zero trust is also about having zero assumptions,” he said.
Further reading: Best Zero Trust Security Solutions








