Compared to other operating systems, Linux patch management is unique because of its open-source nature, which enables a sizable community of developers and security professionals to find vulnerabilities, examine the code, and submit patches.
Linux distributions use package managers to make it easier for users to install software packages and updates. These packages automate the download, installation, and dependency resolution process, which simplifies the process of patch application. While popular Linux distributions can be as easy as Windows to update, many enterprises and organizations prefer to test patches and manage their distribution, creating many of the same issues that admins face with closed-source operating systems.
Here we’ll discuss how patch management works on Linux, best practices, and the best patch management tools for Linux.
- How Patching on Linux Is Different
- Common Linux Patch Management Issues
- How Popular Linux Distributions Handle Patching
- Linux Patch Management Best Practices
- Top Linux Patch Management Tools
How Patching on Linux Is Different From Other Systems
When comparing patch management between Linux and proprietary operating systems like Windows and macOS, there are several key differences to consider.
The open-source nature of Linux means its source code is freely available and fosters a large community of security researchers and developers who actively contribute to vulnerability discovery, patch development and distribution. Package managers make it easier to update software packages and apply updates and patches, and different Linux distributions have their own patching processes and practices. The Linux community actively participates in identifying bugs, developing patches, and testing them, resulting in a collaborative and comprehensive patching process. Organizations using Linux in critical applications will typically have experienced administrators who can apply patches and updates, either manually, via package manager, or automatically.
With closed-source operating systems like Windows, security researchers and others might find and submit bugs to Microsoft, but the source code is not freely accessible and patch development is primarily managed by Microsoft, with Windows Update the mechanism that delivers patches and updates to users. Microsoft releases patches on Patch Tuesday, a scheduled monthly update release. Microsoft performs extensive testing on patches before releasing them to the public.
MacOS and iOS are also a closed ecosystem, with Apple maintaining complete control over the software and patching process. Apple releases patches and updates for macOS and iOS devices periodically, usually alongside new feature releases. The company typically places a high priority on security and swiftly addresses vulnerabilities through patches.
Linux’s open-source nature, package managers, community involvement, and flexibility create its own patch management cadence and challenges, with admins handling patches and updates, sometimes via command line. Microsoft and Apple can automatically update devices for users, although admins sometimes prefer to test and manage updates to ensure that everything works smoothly. Windows focuses on regular cumulative updates and extensive testing, while macOS and iOS emphasize a closed ecosystem and controlled release schedule with a strong emphasis on security.
Each operating system has its own unique approach to patch management based on their underlying philosophies and target audiences. There are patch management tools that can help manage all those operating systems and more; we’ll get to those later on.
Also read:
- Patch Management vs Vulnerability Management: What’s the Difference?
- Top Vulnerability Management Tools
Common Linux Patch Management Issues
Patching all the devices and software in an organization can be challenging regardless of the underlying operating system. While some of these issues also apply to closed-source operating systems, Linux can pose unique patch management challenges because of its open source nature, wide range of distros, and its use in critical applications.
1. Lack of centralized repository for updates
While Linux distros often have a feed and devices can simply receive patches, the absence of a centralized repository for updates can make it challenging for an organization to efficiently distribute and manage patches across multiple systems and distros. To fix this, organizations can set up a local package repository using tools like apt-mirror or Spacewalk. This can be used to store and distribute updates to all relevant systems and provide a centralized location for patch management.
2. Time-consuming patching process
Patching on Linux systems can be time consuming, especially when dealing with a large quantity of endpoints. Manually updating each system can be tedious, complex and prone to human error. There are automation tools that can be employed to significantly reduce the time required for patching. These tools allow for the central management and deployment of patches across multiple systems simultaneously, streamlining the process and saving time.
3. Downtime
Patching Linux systems usually requires restarting or rebooting the entire system, and this can result in downtime. As Linux is widely used in enterprise and cloud environments, this can cause a problem for critical systems that need to remain operational and running. To minimize downtime, organizations can implement techniques like live patching that allows patches to be applied without the need for system restarts or reboots. In addition, utilizing high-available setups and load balancing ensure that services remain accessible during the active patching process.
4. Missing endpoint visibility
Having limited visibility into the status of endpoints can make it difficult to assess the patching status of each system. Implementing centralized monitoring solutions can help provide real-time visibility into patching status of all endpoints. These tools can generate alerts and reports that enable administrators to identify and address any systems that are not properly patched.
5. Difference of systems and applications
Linux environments often consist of various distributions, versions, and configurations that lead to differences in systems and applications. This diversity can make it challenging to apply patches uniformly across endpoints. One potential solution is to standardize the Linux distributions and configurations within the organization. By minimizing the number of variations, it becomes easier to test and apply patches consistently. Additionally, leveraging configuration management tools can help maintain a standardized environment and simplify the patching process.
6. Scattered endpoints due to remote or hybrid work
Remote and hybrid work setups will result in scattered endpoints across different locations, adding to patching difficulty. Employing a remote management solution can help manage and patch systems regardless of the physical location of the device.
7. Automating patches can be challenging
Performance difficulties on the target systems might occasionally result from resource-intensive automated patching procedures. Administrators can reduce the effect on system resources by scheduling patching tasks at off-peak times. Additionally, streamlining the patching process and adopting automation technologies that are resource-friendly will help save resources and provide a more seamless patch rollout.
Also read: 11 Key Steps of the Patch Management Process
How Popular Linux Distributions Handle Patching

Debian
Debian, the mother of various Linux distributions like Deepen, Ubuntu and Mint, employs a unique approach to patch management that sets it apart from the others. Debian’s patch management revolves around its robust package management system, known as Advanced Package Tool (APT). This system handles the retrieval, installation, and maintenance of software packages, including patches and updates. Debian’s development process focuses on thorough testing and quality assurance, aiming to deliver reliable and stable software to its users. The Debian community places a strong emphasis on transparency and collaboration, and Debian maintains a dedicated security team responsible for promptly addressing vulnerabilities and providing security patches. Debian’s long-standing history and reputation as a reliable and stable distribution have contributed to its meticulous approach to patch management.

Ubuntu
Ubuntu is a popular Linux distribution that has built-in patch management mechanisms. It uses the Advanced Package Tool (APT) as its package management system, which provides regular updates and security patches throughout its official repositories. The Ubuntu Update Manager, AKA update manager, provides a graphical interface for managing updates and patches. Additionally, the Ubuntu Security Notices (USN) system provides detailed security advisories and alerts about vulnerabilities and corresponding patches. Ubuntu’s patch management approach focuses on delivering timely updates, security patches and bug fixes to ensure the stability and security of the system. It provides a user-friendly interface and command-line tools to simplify the process of managing and applying patches, making it accessible to both beginners and experienced users.

Gentoo
The patch management mechanism used by Gentoo Linux is distinct from the conventional patch management techniques used by other distributions. Gentoo uses a rolling-release paradigm, in which users receive updates and packages that are regularly updated. It makes use of Portage, a package management system that enables users to compile and modify applications from source code. The Gentoo community maintains a sizable collection that contains Gentoo-specific fixes for security flaws, defects, and the addition of functionality. Through the emerge command, Gentoo also offers a powerful mechanism for handling package updates and security fixes.
Compared to centralized patch management solutions, Gentoo’s patch management system takes more manual work, but it also gives a high level of flexibility and control over the patching process. Users can apply patches where they can tailor software configurations and fine-tune their system according to their needs.
Linux Patch Management Best Practices
There are a number of best practices that can help admins manage the Linux update process. Many of these also apply to closed-source operating systems and applications. See Patch Management Best Practices & Steps for an in-depth guide to patch management.
Monitor and update regularly
Monitor any Linux distribution you use for security advisories, bug fixes, and patches, and update promptly. It’s essential to keep Linux distributions and applications — or any software, for that matter — updated to stay safe from known vulnerabilities. Regular monitoring makes sure that any security advisories, bug fixes, or patches are quickly recognized and deployed.
Prioritize patches
Assess the risk and impact of applying patches to ensure security and system stability. Patch deployment priorities are determined by assessing possible risks and effects of each patch. By concentrating on crucial patches that fix serious flaws or have a significant influence on system stability, system administrators may make sure that resources are used effectively and that possible disruptions are kept to a minimum.
Test patches
Test patches in a controlled environment to identify conflicts, compatibility issues, or unexpected behavior. Patches should be tested to find any conflicts, incompatibilities, or unexpected behavior before applying them to the live system. By properly validating and verifying the system during this testing step, the chance of adverse effects on system functioning or performance is decreased.
Establish patching policies and procedures
A patch management policy is critical for any organization regardless of operating systems or application, and policy and procedures should define roles and responsibilities too. Clear, written patching rules and processes will help ensure success by making processes repeatable, and roles and responsibilities will make it clear who is responsible for patch deployment, testing, and monitoring, promoting efficient collaboration and reducing ambiguity.
Also read: Patch Management Policy: Steps, Benefits and a Free Template
Use a patch management system
Implement a centralized patch management system to automate and streamline the patch deployment process. A patch management tool can save on manual work, enables effective patch distribution across multiple systems, and gives centralized control and insight over the patch management lifecycle.
Create backups
Creating system backups before applying fixes will let you restore to a known working state in case of issues or failures during patching. Backups guarantee that important information and configurations can be recovered, preventing any interruptions or data loss that may result from patch deployments gone wrong. Many patch management tools contain rollback functions that accomplish the same purpose.
Keep records
In order to trace the history of installed patches, monitor for compliance, and provide evidence for audits or investigations, it is important to keep thorough records of patch-related actions. Patch management procedures should be regularly evaluated and audited to verify process effectiveness, identify potential improvement areas, and maintain a proactive and strong security posture.
Train your staff
Educate and train staff on the importance of patch management, best practices, and the risks of delayed patching. Raising awareness of the vital function patches play in ensuring system security makes staffers more aware of best practices, such as prompt patch distribution and the possible hazards connected to neglected or delayed patching, helping to build an organizational culture of proactive security.
Three Top Linux Patch Management Tools
Patch management tools have increased their support for Linux greatly over the years; most of our picks for the Top Patch Management Tools support Linux, but these three are among the most popular for Linux environments.

ManageEngine Patch Manager Plus
ManageEngine Patch Manager Plus is a comprehensive patch management solution that supports different operating systems, including Linux. Administrators can automate patch deployment, plan patching jobs, and keep track of patch compliance with the help of its centralized patch management features. A variety of capabilities are available with ManageEngine such as vulnerability detection, patch testing, and patch rollback options. To monitor patching status and compliance across the enterprise, it also offers comprehensive reporting and analytics.
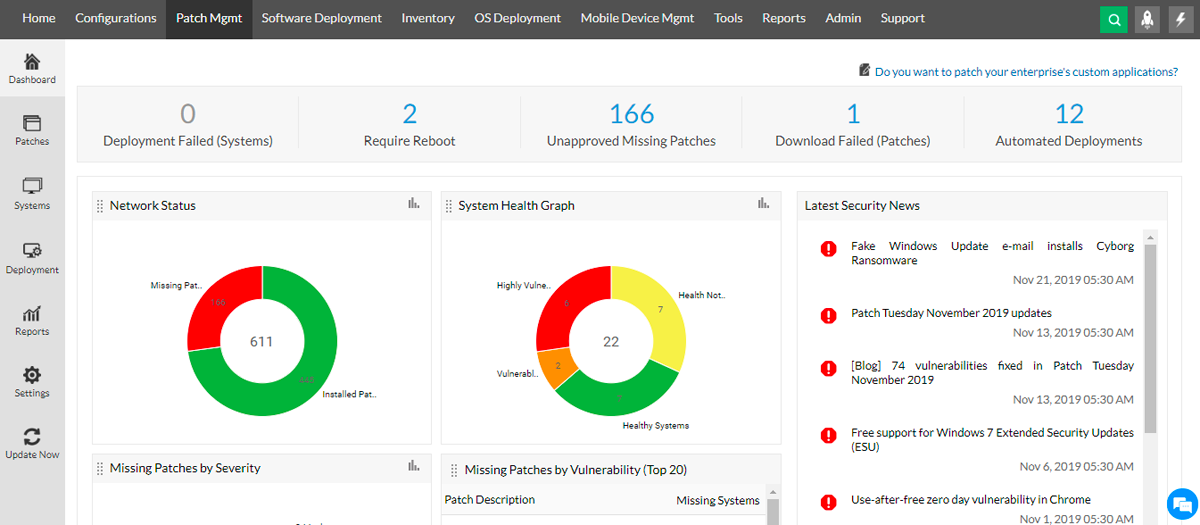
Pros
- Thorough patch testing: Prior to distribution, each patch is rigorously tested to ensure compatibility and stability
- Cloud-based or on-premises deployment
- Complete hardware management: Supports BIOS and hardware driver updates
Cons
- Reporting functionality could offer more thorough insights
- Users would like to see faster support response
- Absence of prior client version upgrades: Better planning and preparation would be possible with prior knowledge of client version upgrades
Pricing
ManageEngine provides a wide range of pricing options. Professional plans start from $245/year up to $24,295/year. Enterprise plans range from $345/year to $37,425/year. The pricing structure takes into account different factors such as the number of servers and computers to be managed. More detailed information on ManageEngine pricing can be found here.

NinjaOne Patch Management
Another patch management program that supports Linux distributions is NinjaOne Patch Management. It offers a simple user interface for managing patches on various Linux platforms. NinjaOne focuses on automating patch detection, download, and deployment in order to streamline the patch management process. To make patch management activities more efficient, it provides patching policies, reporting, and monitoring functions.

Pros
- Effective patch management: Users like the proactive handling of important security updates, ensuring a strong security posture
- Modern and user-friendly: The platform is praised for its modern interface, ease of use, and seamless integration with other products.
- Comprehensive IT asset monitoring: Users appreciate the software’s ability to monitor and manage their IT assets and network effectively.
Cons
- Steep learning curve for non-technical users: Some features may be intimidating for those unfamiliar with Group Policy editing, Command Prompt, or PowerShell.
- Missing features: Users mention the absence of cross-organization user accounts and SAML SSO, although these are planned for future updates.
- 2FA Requirement: Configuration and policy changes require 2FA (Two-Factor Authentication), which can be seen as an inconvenience by some users, even as it’s a good security feature.
Pricing
NinjaOne Patch Manager doesn’t reveal pricing but is seen by users as reasonable and flexible. The Remote Monitoring and Management (RMM) vendor has a “Pay-per-device” monthly pricing structure. You can get a custom patch management quote directly from their pricing page.

Red Hat Enterprise Linux
Popular enterprise-grade Linux distribution Red Hat Enterprise Linux comes with its own patch management system. RHEL handles patching using the Red Hat Network (RHN) or the pay-per-use Red Hat Satellite. Administrators may access and distribute fixes across RHEL systems using a framework for centralized administration that is offered by RHN and Red Hat Satellite. Additionally, Red Hat offers package managers like Dandified Yum (DNF) that makes it simple for users to manage and deploy changes from the official Red Hat repositories. RHEL concentrates on giving its clients enterprise-level support, reliability, and security upgrades.
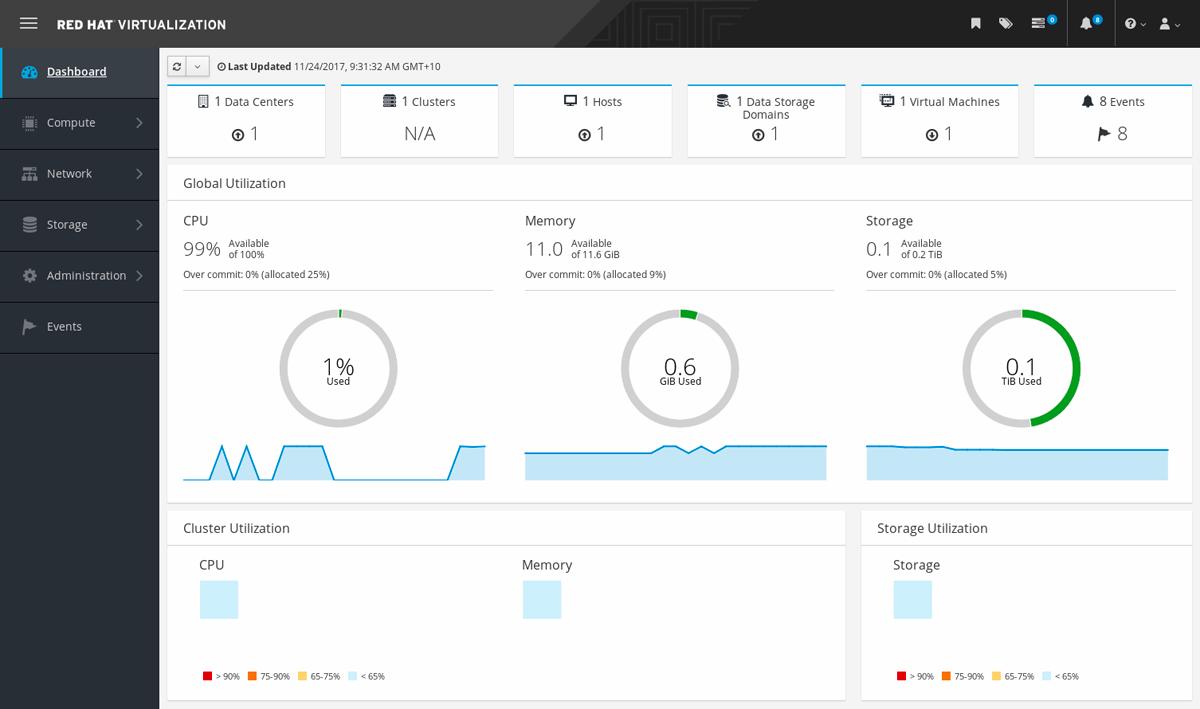
Pros
- Effective system resource management: The program efficiently controls the use of system resources, limiting excessive resource consumption and reducing the chance that other programs may be affected by software crashes.
- Software development is simple because of the distribution’s hassle-free installation of numerous programming languages, which makes it simple for programmers to create and build code in the languages of their choice.
- Simplified device communication: It is simple and user-friendly to access and utilize drivers for a variety of devices, including serial and networked devices.
Cons
- Improved software dependency management: The management of software dependencies could be improved by making it easier to identify package dependencies and the packages that depend on particular components.
- Command-line configuration: Improving the command-line configuration of some packages, especially those that are traditionally set via the GUI, would be beneficial.
Pricing
The cost of Red Hat Enterprise Linux (RHEL) patch management is determined by various factors, such as the number of systems or subscriptions required and the level of support needed. Red Hat offers a range of subscription plans, each with its own pricing structure and support options. The Red Hat Enterprise Linux Workstation subscription starts at $179/year, while the Red Hat Enterprise Linux for Virtual Datacenters subscription is priced at $3,999/year. Red Hat also provides add-ons to complement your subscription and meet additional needs.
To obtain detailed and up-to-date pricing information for Red Hat Enterprise Linux patch management, visit Red Hat’s official website. There, you can find comprehensive information about subscription plans, pricing details, and additional add-on offerings.
Bottom Line: Linux Patch Management
Linux is at the heart of some of the most critical on-premises and cloud environments, so maintaining the open-source operating system is a critically important cybersecurity practice. Organizations can significantly improve their security posture by monitoring and regularly updating their Linux distributions, prioritizing patches, testing in controlled environments, establishing policies, implementing centralized patch management tools, creating backups, maintaining records, and training staff. A trustworthy patch management solution can help guarantee timely updates, expedite procedures, and safeguard important systems from new risks.
Further reading: